A French hacker has raided vulnerable cyber crime forums by exploiting the Heartbleed OpenSSL vulnerability.
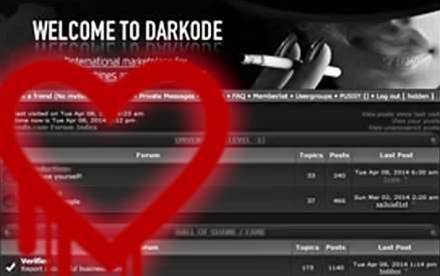
The cybercrime and malware researcher known as Xylitol (@Xylitol) exploited the headline-making vulnerability (CVE-2014-0160) to steal user sessions on the infamous private crime forum Dark0de and targeted online marketplace damagelab.org.
Dark0de is a well known in security quarters for its closed-circle marketplace, where crackers and carders sell malware, exploit kits and stolen credit cards.
In a video posted to YouTube, Xylitol demonstrated exploiting the bug to hijack random user sessions on the forum.
Using the Heartbleed bug, Xylitol was able to gain access to closed areas of the site reserved for trusted members who share stolen credit cards and black market wares.
The hacker demonstrated a similar hack against damagelab.org, prompting it to reset passwords. Both forums were forced to patch against the Heartbleed bug.
The vulnerability within the OpenSSL cryptography library made global waves after it was publicly revealed on 7 April via OpenSSL's mailing list and advisories, as well as a variety of security blogs.
Xylitol, who says he works by day on a manufacturing assembly line and targets malware writers and crime forums by night, first hacked Dark0de last year. He dumped scores of forum posts and private messages between hackers trading in the top-dollar black market for zero-day exploits and malware.
The hacker regularly examines the contents of botnet control panels and malware on his website XyliBox.
The former software pirate has also forged a habit of cracking ransomware platforms which encrypt user data by publicly disclosing the respective decryption key that criminals would only hand over after payment of a ransom.
Heartbleed was first discovered around 21 March by Google security researcher Neel Mehta, and quickly patched for the company's services.
Details of the vulnerability were quietly reported between researchers and companies via non-disclosure agreements until it went public around two weeks later.
Chief security strategist at Fortinet Derek Manky said more computer emergency response teams should have been alerted to the existence of Heartbleed before it was publicly disclosed, to minimise risk to major organisations and agencies.
"From product security point of view, (vulnerability reporting) is not easy -- if we report something to Microsoft and Adobe they will notify their customers, but with open source, there are so many different players," Manky said.



_(33).jpg&h=140&w=231&c=1&s=0)
_(28).jpg&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)





 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 Melbourne Cloud & Datacenter Convention 2026
Melbourne Cloud & Datacenter Convention 2026
 The 2026 iAwards
The 2026 iAwards












_(1).jpg&h=140&w=231&c=1&s=0)



