Amazon Web Services (AWS) is urging developers using the code sharing site GitHub to check their posts to ensure they haven't inadvertently exposed their log-in credentials.

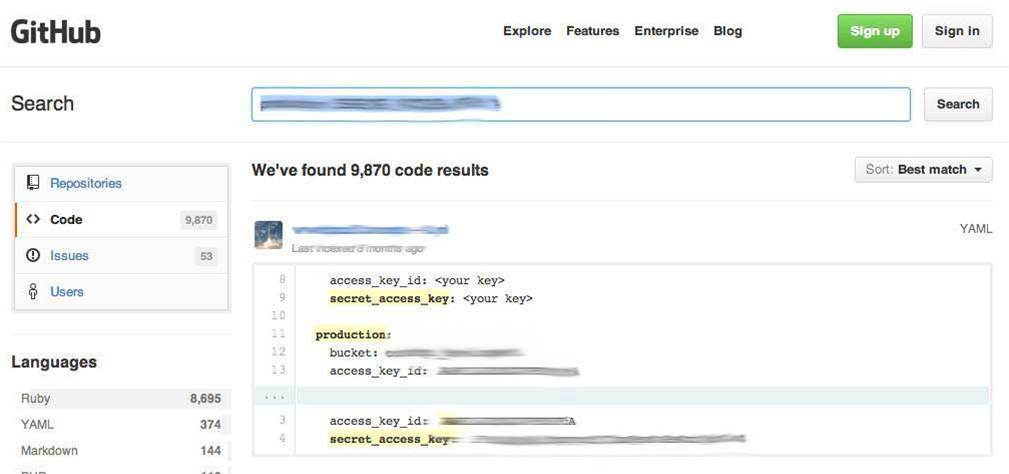
Thousands of ‘secret keys’, which unlock access to private Amazon Web Services accounts are currently available unencrypted to members of the public with just two clicks of a mouse.
The secret keys are issued by Amazon Web Services when users open an account and provide applications access to AWS resources.
When opening an account, users are told to “store the keys in a secure location” and are warned that the key needs to remain “confidential in order to protect your account”.
AWS reminds subscribers that "anyone who has your access key has the same level of access to your AWS resources that you do. Consequently, we go to significant lengths to protect your access keys, and in keeping with our shared-responsibility model, you should as well."
However, a search on GitHub reveals thousands of results where code containing AWS secret keys can be found in plain text, which means anyone can access those accounts.
“You can basically think of them as a username and password - they provide authentication to AWS services," said Ty Miller, founder of penetration testing firm Threat Intelligence.
“Anyone who has access to those keys has access to that particular AWS account. From a security perspective it means they can basically go in and gain access to any of the files that are stored in the AWS account."
Miller decided to test an account at random to see if the key was valid. Below are two screenshots where Miller accessed the account, uploaded a text file to the service and then deleted it again.
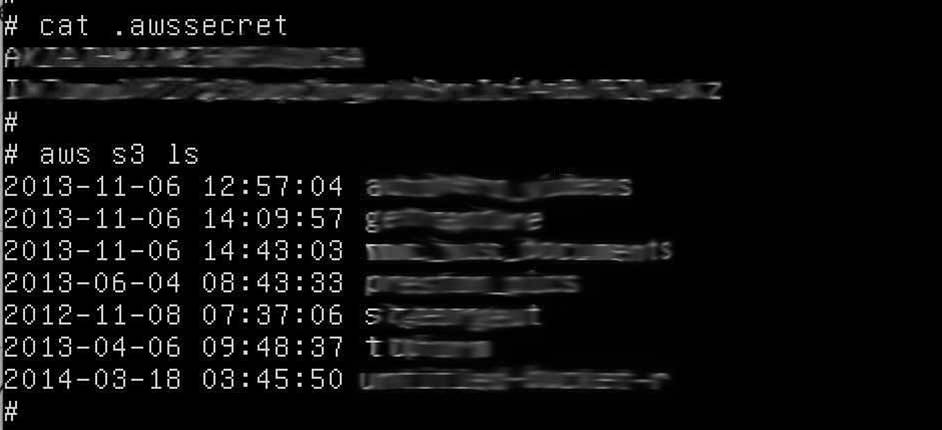
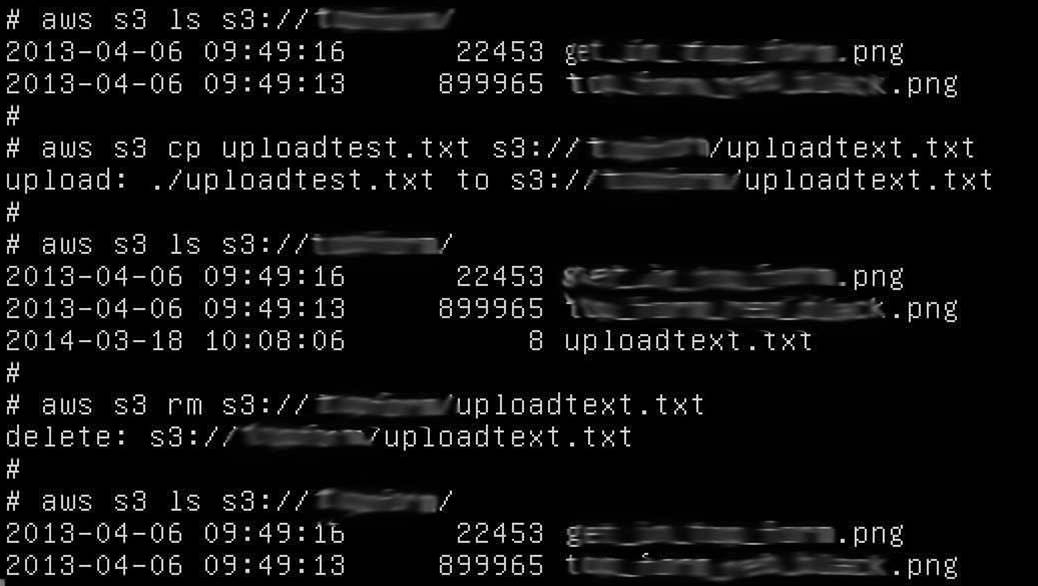
According to Miller, he had access to the account and there was nothing to prevent him deleting files and trashing entire accounts.
“These guys aren’t thinking about the impact of uploading their code to GitHub and having their AWS accounts exposed to everyone on the internet. It can have a pretty significant impact," he said.
"If these are developers who are creating applications for corporations and the corporations AWS keys are leaked - you could potentially go in and delete their entire environment."
So why are all these keys exposed on GitHub?
GitHub is a community site where developers post their code and allow collaboration from other interested devs. The problem is developers aren’t taking enough care to ensure their credentials are properly protected.
Several bloggers have admitted getting a shock after recieving a large bills for bandwidth usage they didn't initiate. For example, Luke Chadwick was hit with a US$3493 (A$3842) bill in December, because of unauthorised activity. To his relief, this was later refunded by AWS.
Earlier this year, AWS contacted Rich Mogull, analyst and CEO of Securosis after three days of unusual activity on his account had run up US$500 in charges. In a blog post from January, Mogull said he had mistakenly published his AWS secret key on GitHub.
"I did not completely scrub my code before posting to GitHub. I did not have billing alerts enabled ... This was a real mistake ... I paid the price for complacency," he admitted in his blog.
In a statement, AWS told iTnews it "takes security very seriously and provides many resources, guidelines and mechanisms to help customers configure AWS services and develop applications using security best practices."
"However, developers are responsible for following our guidance and utilising those mechanisms. When we become aware of potentially exposed credentials, we proactively notify the affected customers and provide guidance on how to secure their access keys," the statement said.


_(22).jpg&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)
.png&h=140&w=231&c=1&s=0)




_(26).jpg&w=100&c=1&s=0)

 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition











_(1).jpg&h=140&w=231&c=1&s=0)



