The volume of internet traffic attributable to the use of Network Time Protocol for giant denial of service attacks is at an all-time high and shows few signs of abating, thanks largely to unprotected servers in many countries, including Australia.

NTP reflection was used as an attack method in February this year, in what was considered the world's hitherto largest DoS attack. It generated over 400Gbps of traffic, which slowed networks around the world.
While the technique behind the NTP DoS reflection attacks has been known for several years, it wasn't until this year that it was widely used.
The NTP protocol is commonly used to syncronise time servers across the globe.
Arbor Networks pegged the usual volume of traffic used to sync time servers at one to two gigabit per second at the beginning of December 2013.
Between January and March this year however, NTP traffic levels shot up to massive levels, reaching a peak on March 4 of 800Gbps, and have remained at high volumes, Arbor Networks claims.
Attackers have quickly learnt to use NTP in easy denial of service attacks that require little bandwidth on their part, but which can completely inundate the network of a victim.
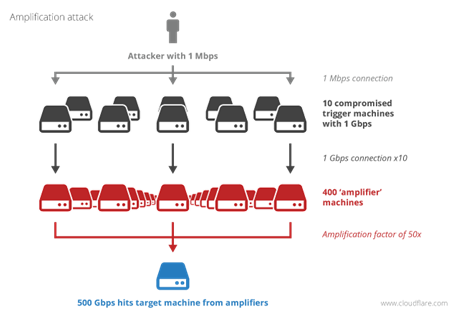
Insecure time servers can amplify traffic 58-fold or more because NTP uses the stateless User Datagram Protocol (UDP) and because responses from the time service are much larger than queries to it.
This means an attacker with just a few megabits of bandwidth can - through NTP reflection - create traffic hundreds of gigabits in size. That traffic can be directed at victims’ networks as UDP packets are easily spoofed with altered source addresses.
In some cases, a single 220-byte UDP packet can generate a response of one hundred 468-byte packets. This large amplification factor means an anonymous attacker can slow down or even take out victim networks with a relatively small amount of initial bandwidth.
Source: Cloudflare
To close NTP servers used for DoS attacks, the Network Time Foundation has set up the Open NTP Project website. The site lets operators scan their networks for abuseable NTP servers and provides advice on how to secure them.
Sample queries of large Australian networks such as Telstra Global by iTnews provided a great many responses, indicating that local providers need to take action to secure their servers.
NTP servers on several Australian networks were involved in February's giant DDoS attack, including iiNet, which has since taken steps to prevent future abuse attempts.
"iiNet was aware of the distributed denial of service involving NTP services. This posed no risk to customer details or security but there were attempts to make services unavailable to customers," the company said.
The ISP's engineers have "put in place measures to mitigate future instances, and preventative solutions are in place," said Roger Yerramsetti, iiNet's operations manager for network services.



.png&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)







 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition
 iTnews Benchmark Awards 2026
iTnews Benchmark Awards 2026
 iTnews Cloud Covered Breakfast Summit
iTnews Cloud Covered Breakfast Summit
 The 2026 iAwards
The 2026 iAwards











_(1).jpg&h=140&w=231&c=1&s=0)



