There's a sign at Google asking employees to check their corporate networks and Windows PCs at the door.
It reflects the position of the world's biggest search engine that perimeter defence and its respective gadgetry is a dead duck.
It also points to a decision by Google to ditch the popular operating system as a result of the 2009 state-sponsored Operation Aurora attacks.
Google staff now can use Windows PCs only with a business case making the company the world's biggest Apple shop with 43,000 devices -- a thousand more than its total staff count.
Engineers Jan Monsch and Harald Wagener provided insight into the company's aptly named Beyond Corp project to dump the corporate network model.
It was a model based on zero trust that splashed encryption everywhere and let staff access corporate resources over McDonald's WiFi.
"We want to completely get rid of the idea of having some sort of perimeter," Wagener said.
"Effectively, firewalls don't help and a lot of other gatekeeper tools that rely on a perimeter simply don't help."
Together with fellow Swiss Googler Monsch, he told the LISA 2013 conference that Google was removing all traces of the old form of privelege associated with the bygone corporate network model.
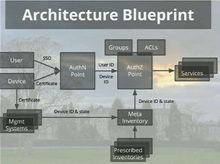
Instead, Google would authenticate and authorise users only after their devices have been verified as belonging to the Google inventory and as being in a secure state.
Finding a way to know how many devices Google has at any given time was a two-year thorn in the side for Monsch. So Google uses what it calls meta-inventory, which connected to upstream inventory sources and provided an interface for authorisation each time users attempted to connect.
"Inventory in [most] organisations is a data dump - often manually curated and no one looks in it to see if the data is correct," Monsch said.
An inventory needed to undergo "gory" cleaning to ensure accuracy. Once this was done, certificates could be issued to authenticated users.
Google was implementing the new platform on the existing legacy architecture in a bid to get users to migrate over to what it says is a more efficient system.
This presented challenges in systems management and latency with legacy systems such as synchronous network attached storage which was swapped to asynchronous cloud models.
"It is really important to build support in your organisation and reach all the people targeted with the program," Monsch said, adding executive backing was also critical.