Update: A proof of concept (POC) exploit of the deadly RDP vulnerability has been shown to trigger blue screens of death on Windows XP and Windows Server 2003 machines.
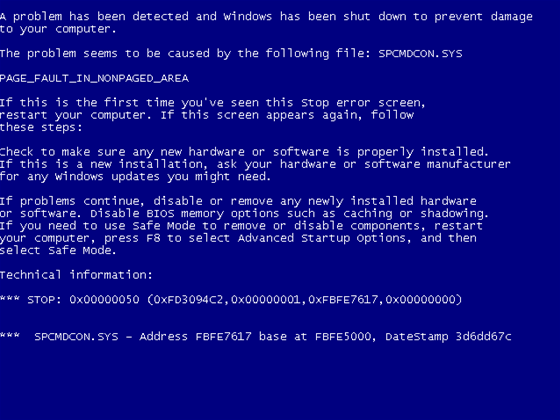
Two POCs were described as accurate in an email to SC by the discoverer of the vulnerability, Luigi Auriemma.
A third which was circulating on Twitter was fake.
HackLabs penetration tester Jody Melbourne said tests of the Chinese POC had crashed Windows virtual machines.
A bounty for a working exploit has been posted on developer site Gun.IO, funded in part by Metasploit creator HD Moore.
Auriemma said in a tweet that the packet stored in the Chinese rdpclient.exe POC was the "exact one" which he submitted to the Zero Day Initiative.
Some researchers said the source was the Microsoft's Active Protections Program.


.png&h=140&w=231&c=1&s=0)
_(23).jpg&h=140&w=231&c=1&s=0)
_(20).jpg&h=140&w=231&c=1&s=0)




_(26).jpg&w=100&c=1&s=0)
 iTnews Executive Retreat - Security Leaders Edition
iTnews Executive Retreat - Security Leaders Edition












_(1).jpg&h=140&w=231&c=1&s=0)



