When Robert Oppenheimer saw the Trinity atom bomb test in July, 1945, he was reminded of a Hindu scripture: "Now I am become Death, the shatterer of worlds".
In quoting from the Bhagavad Gita, Oppenheimer, father of the atom bomb, was voicing what anyone who has created a significant technology has surely felt at one time or another. Now that the Golem has been set free, what will it do? Will it be turned to peaceful purposes or will it be abused?
The technology improves but the motivations for wrong-doing stay the same. When John Dillinger and his gang robbed US banks in the '30s, he donned disguises and wielded machine guns to steal what was then about US$300,000.
Fast forward to last year and a 'global cashout conspiracy' allegedly led by Israeli hacker Ehud Tenenbaum hit US financial networks for US$10 million.
In that case, despite the changing times, fraud and theft are the same. It's just that the Information Age provides easier access to more data than ever before.
Richard Lucas, who researches ethical issues in IT at the Australian Centre for Applied Philosophy and Public Ethics, says today's crimes differ from their low-tech predecessors in by scale and ease.
"I'm not sure if stealing a million credit card details is any worse than stealing one," he said. "The only difference is one of scale."
The added efficiency of IT could, in some cases, mean an hours-long shutdown of a country's online banking and day-to-day operations. In other cases, it could enable governments to hunt for dissidents by broadly monitoring local voice telecommunications.
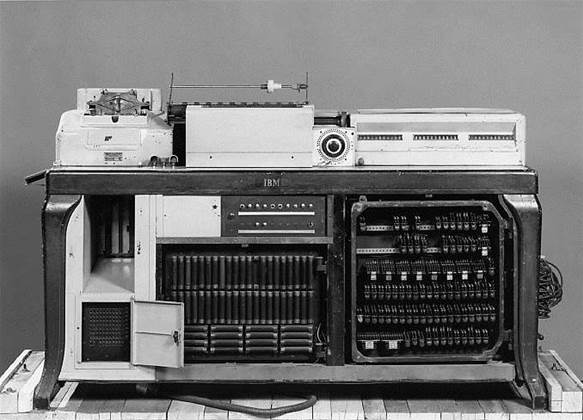
Edwin Black, who investigated the relationship between IBM and Nazi Germany for his investigative book IBM and the Holocaust, wrote that IT such as the Hollerith tabulating machine pictured on this page enabled the Nazis to identify and persecute so many, so quickly.
Lucas says that technology suffers from the "dual-use dilemma": it can be used for peace or war.
"Technology does not have any intentions in its own right," he says. "It can be used for good or bad."
He blames a lack of comprehensive, professional regulatory oversight and ethics education for misuse of IT.
Citing the philosophical "moral distance"', which could shield people from feeling morally obligated to issues that seem far away, Lucas says that IT developers are often far removed from their technologies' impact.
"It's a long way from ‘I'm just writing some code' to ‘someone is being denied welfare payments'," he says.
"We often don't know what these things [such as IT and scientific developments] are going to be used for. But, as a scientist, you can have a really good guess about what these things should be used for."
Between disseminating information, enhancing businesses and providing entertainment, IT has its merits. But, as former US President Franklin Roosevelt observed, "Great power involves great responsibility".
iTnews looks at five technologies that were turned to evil ends.
Read on for iTnews' Five evil uses of IT ...
Nokia technology tracks Iranian dissidents
 |
| Protests in Iran |
In the wake of Iran's June presidential election, telecommunications services provider Nokia Siemens Networks (NSN) was accused of providing the Iranian Government with technology to monitor and censor dissidents.
The lawful Intercept capability allows Iran's national telecommunications operator, TCI, to monitor local voice calls on its fixed and mobile networks.
Telecommunications networks are legally required to provide lawful interception in many countries besides Iran, including the US and the EU. In Australia, lawful intercept is governed by the Telecommunications (Interception) Act 1979, which makes it illegal to intercept telecommunications unless under the authority of a law-enforcement warrant.
But Iran's use of such technology may have gone beyond Western standards. Human rights and immigration lawyer Lily Mazaheri told The Washington Post in April that one of her clients was arrested because copies of their instant messages were obtained by the Ministry of Intelligence.
Iran has confirmed more than 4000 arrests and at least 27 deaths in the protests. Protesters are said to be abused in prison. Meanwhile, websites and news media are censored.
NSN says that its lawful Intercept technology adheres to European Telecommunications Standards Institute (ETSI) and 3rd Generation Partnership Project (3GPP) standards.
The company admits to providing Iran with a monitoring facility that enabled law enforcement officers to access the network's lawful intercept capability last year. But it is said to be limited to monitoring only defined phone numbers, and not allow the scanning of network traffic or internet surveillance.
"Nokia Siemens Networks and other companies have delivered mobile networks to Iran over a period of years, long before the recent political developments," the company says in a statement.
"We are, of course, aware of reports from Iran and condemn any abuse of communication technologies that may have taken place."
The company declined to provide further comment for this story.
Read on for four more 'evil uses of IT."
DDoS attacks take Estonia offline

In April, 2007, a three-week wave of distributed denial of service attacks took the websites of Estonian Government ministries, political parties, newspapers, banks, and companies offline.
The cyberattacks were prompted by the country's relocation of the Soviet World War II memorial on April 27 that sparked violent protests in the country's capital, Tallinn.
They began with a 200-fold surge in traffic to Estonian websites, overcrowding the servers' bandwidth capacity by demanding four million packets a second.
The Nashi youth movement in Russia claimed responsibility for the attacks, which ranged from ping floods to botnet spam.
Estonia is considered one of the world's most wired nations, with a reported 40 percent of its citizens reading an online newspaper daily, and more than 90 percent of bank transactions online.
The attacks and their impact prompted NATO to develop a cyber defence policy that was adopted early last year, and to establish a Cooperative Cyber Defence Centre of Excellence in Tallin, which is dedicated to research and training on cyberwarfare.
"The need for a cyber-defence centre is compelling," said General James Mattis, NATO's Supreme Allied Commander Transformation, at the signing ceremony. "It will help NATO defy and successfully counter the threats in this area."
Read on for three more "evil uses of IT"...
Titan Rain prompts fears of cyberwar

Said to be the world's largest instance of state-sponsored cyber warfare, "Titan Rain" was a series of attacks on US Government agency networks.
They began in 2003, and targeted the networks of NASA, the departments of state, energy, homeland security, and defence. The World Bank was also targeted.
Through trojans, spyware, viruses and zombie computers, Titan Rain hackers accessed sensitive information such as specifications for the US Army's helicopter mission-planning systems and flight-planning software for the Army and Air Force.
Because they were traced back to China's Guangdong Province, some suspected the China's involvement. But it is also likely that systems in that country were relay points for attacks from elsewhere.
Although details and the FBI investigation are scarce, the media storm surrounding Titan Rain makes it a turning point for the public perception of cyber warfare.
The US has improved its cybersecurity measures. But China continues to be blamed for new attacks on its networks, including those on the Pentagon in 2007 and an infiltration of US electric grid systems earlier this year.
And according to security expert Bruce Schneier, recent wave of distributed denial of service (DDoS) attacks on US and South Korean websites suggests that cybercrime is far from defeated.
"Are we doing better? The attacks on South Korea say not really," Schneier says.
"Titan Rain was just the one that happened to make the news," he says. "It does seem like something was big and organised, but I'm sure there are others that could be bigger and don't make the paper."
Read on for two more "evil uses of IT"...
Thank the West for Chinese censorship

To those who value freedom of expression and information as basic human rights, China's "Great Firewall" is a travesty.
More than 60 sets of internet regulations govern its ISPs, content producers and users.
They prohibit sexually suggestive, superstitious, anti-socialist material and that which "harms the prosperity and interests of the state".
Known in China as the "Golden Shield Project", the Great Firewall blocks censored material using methods that include: DNS filtering or redirection, IP blocking, URL filtering and packet filtering by keywords.
Eight state-licenced ISPs link its network to the foreign internet backbone, according to the China Internet Network Information Center's 2009 report.
And China encourages businesses and search engines to self-censor with the threat of being blocked or shut down. For instance, Google (founded on the notion that "you can make money without doing evil") displays limited information on search terms such as "democracy" and "Tiananmen Square".
Meanwhile, Yahoo! has handed over data about its users to Chinese authorities, resulting in the arrests of dissidents Li Zhi in 2003 and Shi Tao in 2005.
The company has since moved to mend its ways.
"Yahoo! was one of the first internet companies to enter China and, in acknowledging the challenges we and other companies face in these markets, we have taken concrete steps individually and collectively to protect human rights there and globally," Yahoo! says.
"Yahoo! is committed to protecting fundamental human rights and freedom of expression. We are committed to making sure our actions match our values around the world and this effort has resulted in industry-leading initiatives to advance global privacy and free expression."
The US is testing 'feed over e-mail' technology to evade web screening systems in countries such as China and Iran.
But some argue that without US companies, the Great Firewall wouldn't exist.
At a 2006 US Congressional hearing, Congressman Christopher Smith said: "Cisco has provided the Chinese Government with the technology necessary to filter Internet content.
"For the sake of market share and profits, leading US companies, like Google, Yahoo!, Cisco, and Microsoft have compromised the integrity of their products and their duties as responsible corporate citizens."
But Cisco says it complies with all US Government regulations that prohibit sale to certain destinations, to users who misuse the products or resell them to prohibited users.
"Cisco supports transparency in the way the Internet is used and complies with applicable regulations," a company spokesman says.
Read on for one final "evil use of IT"...
Hollerith and the Holocaust

Blamed for an estimated 11 million deaths of men, women and children, the Nazi party is arguably history's most evil political power.
Under Adolf Hitler's leadership from 1933 to 1945, the Nazis identified ethnic Jews and other minorities or those with disabilities in Central and Eastern Europe for the purposes of genocide through medical experimentation, forced labour and execution.
The task of quickly collecting and organising the vast amount of racial census data may have been impossible if not for the use of relatively new punch-card machines that were invented by German-American Herman Hollerith in the 1890s.
His tabulating machines (pictured), forerunners to today's computers, were used for accounting, tracking inventory and to process US census data. They were developed, made and distributed by the Computing Tabulating Recording Corporation that was later renamed IBM.
IBM and its German subsidiary, Dehomag, leased Hollerith machines and related equipment to the Nazis. According to IBM and the Holocaust author Edwin Black, the five-digit numbers that the machines used to identify prisoners gave rise to the infamous identification tattoos used at the Auschwitz concentration camp.
"There always would have been a holocaust of some kind [even without IBM]," Black says. "But the holocaust that we know, with the astronomical numbers, was the IBM industrial holocaust.
"The Information Age began with the individualisation of statistics, not in Silicon Valley, but in Berlin in 1933," he says.
IBM is suspected to have profited greatly from its dealings with Nazi Germany, including leasing its punch-card machines and printers and supplying the paper that they needed.
IBM has not refuted Black's claims. It claims to have little information concerning operations in Nazi Germany, as most documents were destroyed or lost during the war.
"There has been speculation concerning the use of IBM equipment by Nazi authorities during World War II," says IBM spokesman Doug O'Shelton.
"As with hundreds of foreign-owned companies that did business in Germany at that time, IBM's German operations came under the control of Nazi authorities prior to and during World War II."
"IBM and its employees around the world find the atrocities committed by the Nazi regime abhorrent and categorically condemn any actions which aided their unspeakable acts," he says.
What are some other examples of 'evil uses' of information technology? We'd like to hear your thoughts below...


.png&h=140&w=231&c=1&s=0)






.png&w=120&c=1&s=0) EDUtech AU
EDUtech AU
.png&w=120&c=1&s=0) Security Exhibition & Conference 2025
Security Exhibition & Conference 2025
 Integrate Expo 2025
Integrate Expo 2025
 Digital As Usual Cybersecurity Roadshow: Brisbane edition
Digital As Usual Cybersecurity Roadshow: Brisbane edition
 iTnews Benchmark Security Awards 2025
iTnews Benchmark Security Awards 2025









.jpg&h=140&w=231&c=1&s=0)



